Before removing this right from a group. If groups other than the local Administrators group have been assigned this user right, removing this user right might cause performance issues with other applications. NOTE: Perform this procedure only if the account selected for data collection is not a member of the Domain Admins group. Required Privileges and Permissions - ADAudit Plus.
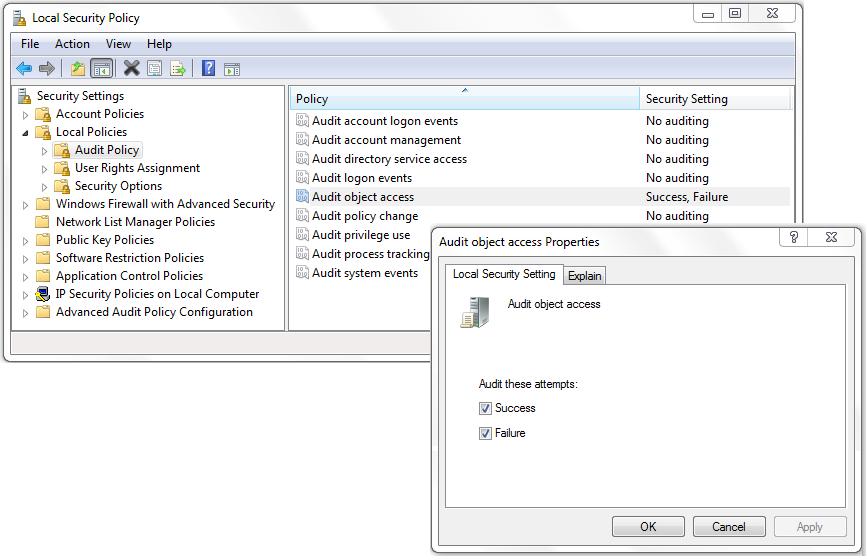
Default assignment: Administrators. This right allows you to: Modify the object level audit policy on files, folders, registry keys, services and any other non Active Directory object. To access the object level audit policy open the object’s. Inappropriate granting of user rights can provide system, administrative, and other high level capabilities.
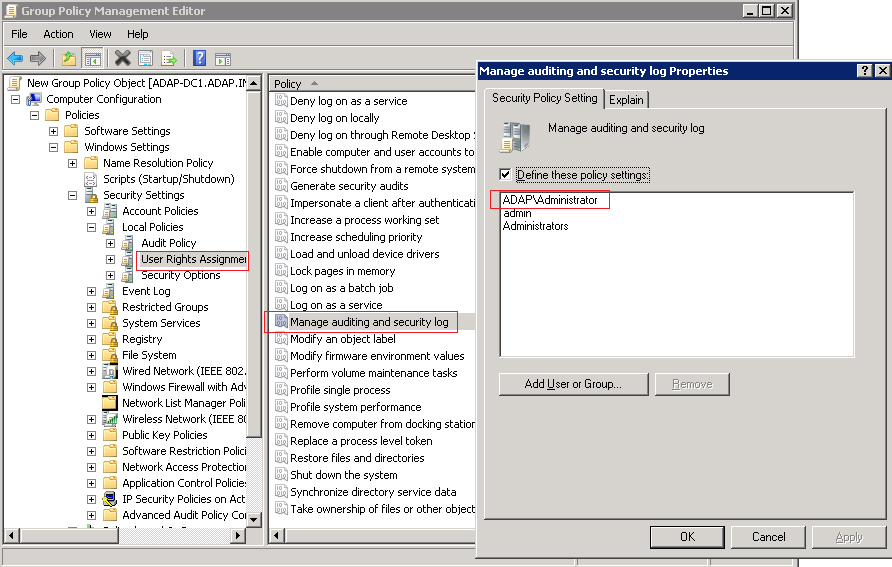
Manage auditing and security log AKA: SeSecurityPrivilege, Manage auditing and security log. This could be used to clear evidence of tampering. Make the user a member of the Event Log Readers group. Members of the event log readers group will be able to read the event logs of all the audited computers. This setting is available in the User Rights Assignments section under Local Policies in the Local Security Policy console.
You can either manage Group Policy locally (gpedit.msc) or via Active Directory by using the Group Policy Management Console (GPMC). Auditing is setup and managed by Group Policy. I highly suggest using the GPMC and manage auditing using Active Directory. Created a security group called Global Event Log Auditors and added our security engineer to that group.
Running as a Standard user is best practice for security purposes and will help protect your computer from infection. After you create CompAdmin, to it and change your regular user account to Standard. Then log back into your regular account. After you configure the auditing policy, events are recorded in the security log. Delegating Access to the Security Log.
If there is a group policy applied on the dc make sure it is not removing this permission. Open Local Security Policy. Security teams must implement a process to audit security events as part of their daily operations. The best way to achieve this is by scheduling reports using a security information and event management (SIEM) tool.
A SIEM tool can parse log data from different event sources—such as servers, domain controllers, firewalls. This site uses cookies for analytics, personalized content and ads. By continuing to browse this site, you agree to this use. Active Directory is one of the most important areas of Windows that should be monitored for intrusion prevention and the auditing required by legislation like HIPAA and Sarbanes-Oxley.
I say that because Active Directory is home to objects most associated with user access: user accounts, groups, organizational units and group policy objects. This policy setting determines which users can specify object access audit options for individual resources such as files, Active Directory. ManageEngine DataSecurity Plus is an agent-based file auditing and reporting software.
In large enterprises, multiple administrators manage objects centrally through the Group Policy Management Console (GPMC) from different computers in the domain. Keep track of changes made to the files, file objects in the folders or sub-folders and shares. Learn to audit file and folder access on publicly accessible computers to test your security policy and determine whether there are any unauthorized uses taking place While auditing file and. To resolve the promotion issue, the following was performed: 1. In this segment Scott demonstrates the difference between the security logs and other events. The auditing of successful and failed attempts is demonstrated with a view of login attempts in the security log.
This video concludes with a demonstration of how to activate other types of security auditing by editing the local policy. Using EventLog Analyzer you can collect all your object access audit logs at a centralized location and manage your object access audit logs effectively. This log management software can track success and failure access attempts on folders and files in your enterprise.
The SACL is part of the security descriptor for an active directory object and specifies which operations should be audited. It is assigned automatically to the Administrators Group. Home Help Search CVE Vulnerability Database Browse. OVAL Objects OVAL Sources By Release Dates.
Log3is an efficient Exchange Server reporting, auditing , and alerting tool.
Hiç yorum yok:
Yorum Gönder
Not: Yalnızca bu blogun üyesi yorum gönderebilir.